-
webhacking.kr 6번 base64와 replace를 이용한 admin 문제WeekHack/WebHacking 2019. 7. 6. 11:17반응형SMALL
안녕하세요. Luke입니다.
웹케알 6번 문제입니다. 100점 짜리 문제더군요. 쉽긴 쉬웠는데 코드짜야되서 귀찮았던 문제입니다.

들어가면 다음과 같이 guest, 123qw가 각각 아이디 패스워드랍니다.
hint가 base64입니다.
일단 소스를 보았습니다.
<?php if(!$_COOKIE[user]) { $val_id="guest"; $val_pw="123qwe"; for($i=0;$i<20;$i++) { $val_id=base64_encode($val_id); $val_pw=base64_encode($val_pw); } $val_id=str_replace("1","!",$val_id); $val_id=str_replace("2","@",$val_id); $val_id=str_replace("3","$",$val_id); $val_id=str_replace("4","^",$val_id); $val_id=str_replace("5","&",$val_id); $val_id=str_replace("6","*",$val_id); $val_id=str_replace("7","(",$val_id); $val_id=str_replace("8",")",$val_id); $val_pw=str_replace("1","!",$val_pw); $val_pw=str_replace("2","@",$val_pw); $val_pw=str_replace("3","$",$val_pw); $val_pw=str_replace("4","^",$val_pw); $val_pw=str_replace("5","&",$val_pw); $val_pw=str_replace("6","*",$val_pw); $val_pw=str_replace("7","(",$val_pw); $val_pw=str_replace("8",")",$val_pw); Setcookie("user",$val_id); Setcookie("password",$val_pw); echo("<meta http-equiv=refresh content=0>"); } ?> <html> <head> <title>Challenge 6</title> <style type="text/css"> body { background:black; color:white; font-size:10pt; } </style> </head> <body> <? $decode_id=$_COOKIE[user]; $decode_pw=$_COOKIE[password]; $decode_id=str_replace("!","1",$decode_id); $decode_id=str_replace("@","2",$decode_id); $decode_id=str_replace("$","3",$decode_id); $decode_id=str_replace("^","4",$decode_id); $decode_id=str_replace("&","5",$decode_id); $decode_id=str_replace("*","6",$decode_id); $decode_id=str_replace("(","7",$decode_id); $decode_id=str_replace(")","8",$decode_id); $decode_pw=str_replace("!","1",$decode_pw); $decode_pw=str_replace("@","2",$decode_pw); $decode_pw=str_replace("$","3",$decode_pw); $decode_pw=str_replace("^","4",$decode_pw); $decode_pw=str_replace("&","5",$decode_pw); $decode_pw=str_replace("*","6",$decode_pw); $decode_pw=str_replace("(","7",$decode_pw); $decode_pw=str_replace(")","8",$decode_pw); for($i=0;$i<20;$i++) { $decode_id=base64_decode($decode_id); $decode_pw=base64_decode($decode_pw); } echo("<font style=background:silver;color:black> HINT : base64 </font><hr><a href=index.phps style=color:yellow;>index.phps</a><br><br>"); echo("ID : $decode_id<br>PW : $decode_pw<hr>"); if($decode_id=="admin" && $decode_pw=="admin") { @solve(6,100); } ?> </body> </html>이렇다고 합니다. 대충 분석해보면 쿠키에 있는 id와 pw를 각각 위의 조건과 같이 replace하고 decode를 20번 합니다.
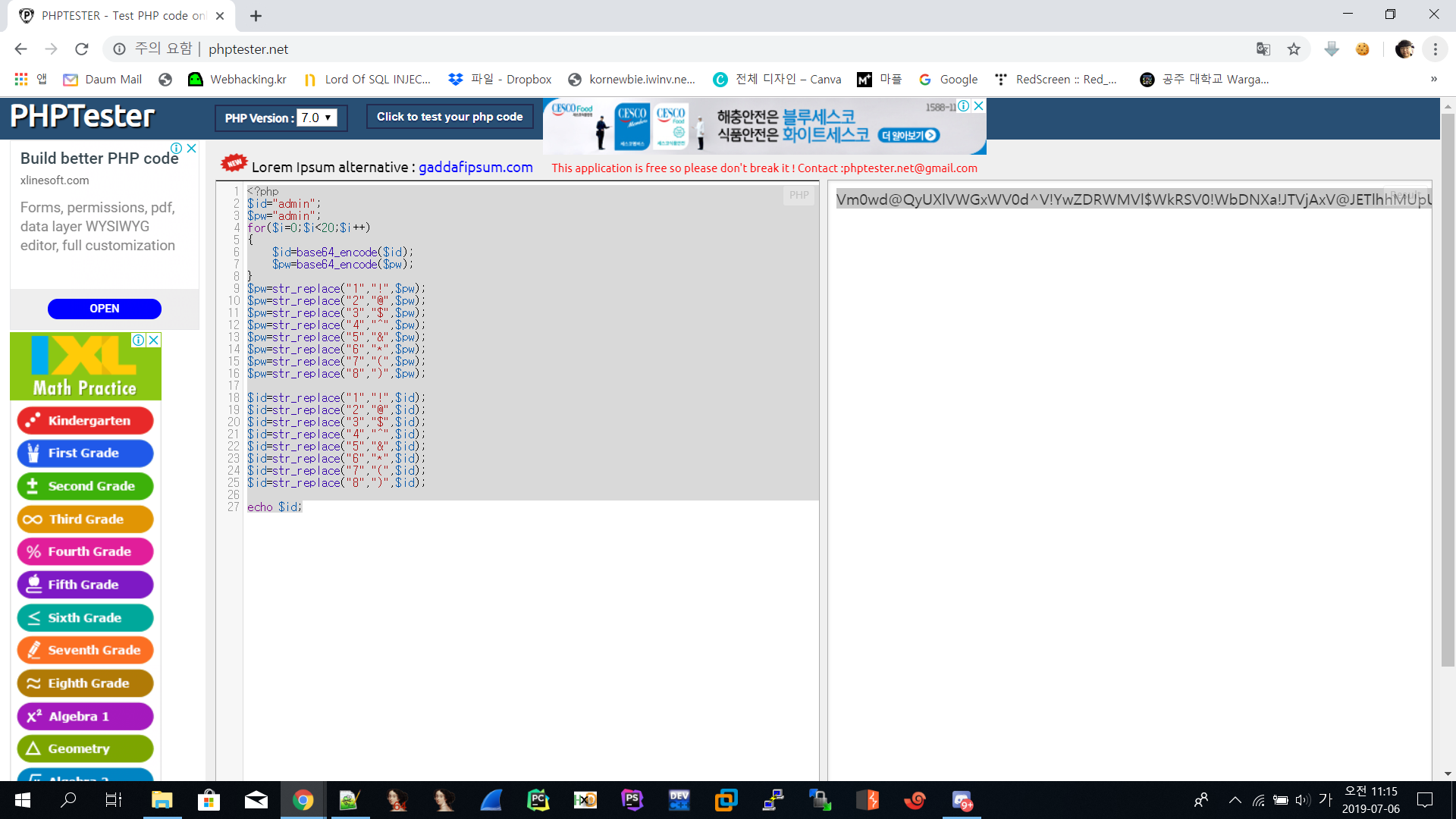
그래서 거꾸로 admin을 저 조건에 맞게 encode하는 코드를 짰습니다.
<?php $id="admin"; $pw="admin"; for($i=0;$i<20;$i++) { $id=base64_encode($id); $pw=base64_encode($pw); } $pw=str_replace("1","!",$pw); $pw=str_replace("2","@",$pw); $pw=str_replace("3","$",$pw); $pw=str_replace("4","^",$pw); $pw=str_replace("5","&",$pw); $pw=str_replace("6","*",$pw); $pw=str_replace("7","(",$pw); $pw=str_replace("8",")",$pw); $id=str_replace("1","!",$id); $id=str_replace("2","@",$id); $id=str_replace("3","$",$id); $id=str_replace("4","^",$id); $id=str_replace("5","&",$id); $id=str_replace("6","*",$id); $id=str_replace("7","(",$id); $id=str_replace("8",")",$id); echo $id;이 소스를 php를 돌려주는 웹에서 돌려봤습니다.
그랬더니
가 나왔습니다.
Vm0wd@QyUXlVWGxWV0d^V!YwZDRWMVl$WkRSV0!WbDNXa!JTVjAxV@JETlhhMUpUVmpBeFYySkVUbGhoTVVwVVZtcEJlRll&U@tWVWJHaG9UVlZ$VlZadGNFSmxSbGw!VTJ0V!ZXSkhhRzlVVmxaM!ZsWmFjVkZ0UmxSTmJFcEpWbTEwYTFkSFNrZGpSVGxhVmpOU!IxcFZXbUZrUjA!R!UyMTRVMkpIZHpGV!ZFb$dWakZhV0ZOcmFHaFNlbXhXVm!wT!QwMHhjRlpYYlVaclVqQTFSMWRyV@&kV0!ERkZVbFJHVjFaRmIzZFdha!poVjBaT@NtRkhhRk&sYlhoWFZtMXdUMVF$TUhoalJscFlZbGhTV0ZSV@FFTlNiRnBZWlVaT!ZXSlZXVEpWYkZKRFZqQXhkVlZ!V@xaaGExcFlXa!ZhVDJOc@NFZGhSMnhUVFcxb@IxWXhaREJaVmxsM!RVaG9hbEpzY0ZsWmJGWmhZMnhXY!ZGVVJsTk&WMUo!VmpKNFQxWlhTbFpYVkVwV!lrWktTRlpxUm!GU@JVbDZXa!prYUdFeGNHOVdha0poVkRKT@RGSnJhR@hTYXpWeldXeG9iMWRHV@&STldHUlZUVlpHTTFSVmFHOWhiRXB*WTBac!dtSkdXbWhaTVZwaFpFZFNTRkpyTlZOaVJtOTNWMnhXWVZReFdsaFRiRnBZVmtWd!YxbHJXa$RUUmxweFVtMUdVMkpWYkRaWGExcHJZVWRGZUdOSE9WZGhhMHBvVmtSS!QyUkdTbkpoUjJoVFlYcFdlbGRYZUc&aU!XUkhWMjVTVGxOSGFGQlZiVEUwVmpGU!ZtRkhPVmhTTUhCNVZHeGFjMWR0U@tkWGJXaGFUVzVvV0ZreFdrZFdWa$B*VkdzMVYySkdhM@hXYTFwaFZURlZlRmR!U@s!WFJYQnhWVzB^YjFZeFVsaE9WazVPVFZad@VGVXlkREJXTVZweVkwWndXR0V^Y0ROV@FrWkxWakpPU!dKR!pGZFNWWEJ@Vm!0U!MxUXlUWGxVYTFwb!VqTkNWRmxZY0ZkWFZscFlZMFU!YVUxcmJEUldNalZUVkd^a!NGVnNXbFZXYkhCWVZHdGFWbVZIUmtoUFYyaHBVbGhDTmxkVVFtRmpNV!IwVTJ0a!dHSlhhR0ZVVnpWdlYwWnJlRmRyWkZkV@EzQjZWa@R*TVZZd0!WWmlla!pYWWxoQ!RGUnJXbEpsUm!SellVWlNhVkp!UW&oV!YzaHJWVEZzVjFWc!dsaGlWVnBQVkZaYWQyVkdWWGxrUkVKWFRWWndlVmt$V@&kWFIwVjRZMFJPV@!FeVVrZGFWM@hIWTIxS!IxcEhiRmhTVlhCS!ZtMTBVMU!^VlhoWFdHaFlZbXhhVjFsc!pHOVdSbXhaWTBaa@JHSkhVbGxhVldNMVlWVXhXRlZyYUZkTmFsWlVWa@Q0YTFOR!ZuTlhiRlpYWWtoQ!NWWkdVa@RWTVZwMFVtdG9VRll&YUhCVmJHaERUbXhrVlZGdFJtcE&WMUl$VlRKMGExZEhTbGhoUjBaVlZucFdkbFl$V@&OT@JFcHpXa@R$YVZORlNrbFdNblJyWXpGVmVWTnVTbFJpVlZwWVZGYzFiMWRHWkZkWGJFcHNVbTFTZWxsVldsTmhWa$AxVVd^d!YySllVbGhhUkVaYVpVZEtTVk&zYUdoTk!VcFZWbGN^TkdReVZrZFdiR!JvVW&wc@IxUldXbmRsYkZsNVkwVmtWMDFFUmpGWlZXaExWMnhhV0ZWclpHRldNMmhJV!RJeFMxSXhjRWhpUm!oVFZsaENTMVp0TVRCVk!VMTRWbGhvV0ZkSGFGbFpiWGhoVm!^c@NscEhPV$BTYkhCNFZrY$dOVll^V@&OalJXaFlWa!UxZGxsV!ZYaFhSbFp&WVVaa!RtRnNXbFZXYTJRMFdWWktjMVJ!VG!oU@JGcFlXV$hhUm!ReFduRlJiVVphVm0xU!NWWlhkRzloTVVwMFlVWlNWVlpXY0dGVVZscGhZekZ$UlZWdGNFNVdNVWwzVmxSS0!HRXhaRWhUYkdob!VqQmFWbFp0ZUhkTk!WcHlWMjFHYWxacmNEQmFSV!F$VmpKS@NsTnJhRmRTTTJob!ZrUktSMVl^VG&WVmJFSlhVbFJXV!ZaR!l*RmlNV!JIWWtaV!VsZEhhRlJVVm!SVFpXeHNWbGRzVG!oU!ZFWjZWVEkxYjFZeFdYcFZiR@hZVm!^d!lWcFZXbXRrVmtwelZtMXNWMUl*YURWV0!XUXdXVmRSZVZaclpGZGliRXB&Vld0V!MySXhiRmxqUldSc!ZteEtlbFp0TURWWFIwcEhZMFpvV@sxSGFFeFdNbmhoVjBaV@NscEhSbGROTW!oSlYxUkplRk!^U!hoalJXUmhVbXMxV0ZZd!ZrdE&iRnAwWTBWa!dsWXdWalJXYkdodlYwWmtTR0ZHV@xwaVdHaG9WbTE0YzJOc!pISmtSM0JUWWtad0&GWlhNVEJOUmxsNFYyNU9hbEpYYUZoV@FrNVRWRVpzVlZGWWFGTldhM0I@VmtkNFlWVXlTa!pYV0hCWFZsWndSMVF^V@tOVmJFSlZUVVF$UFE9PQ==라고 합니다. 그래서 쿠키에 저거 넣고 새로고침을 해보았습니다.
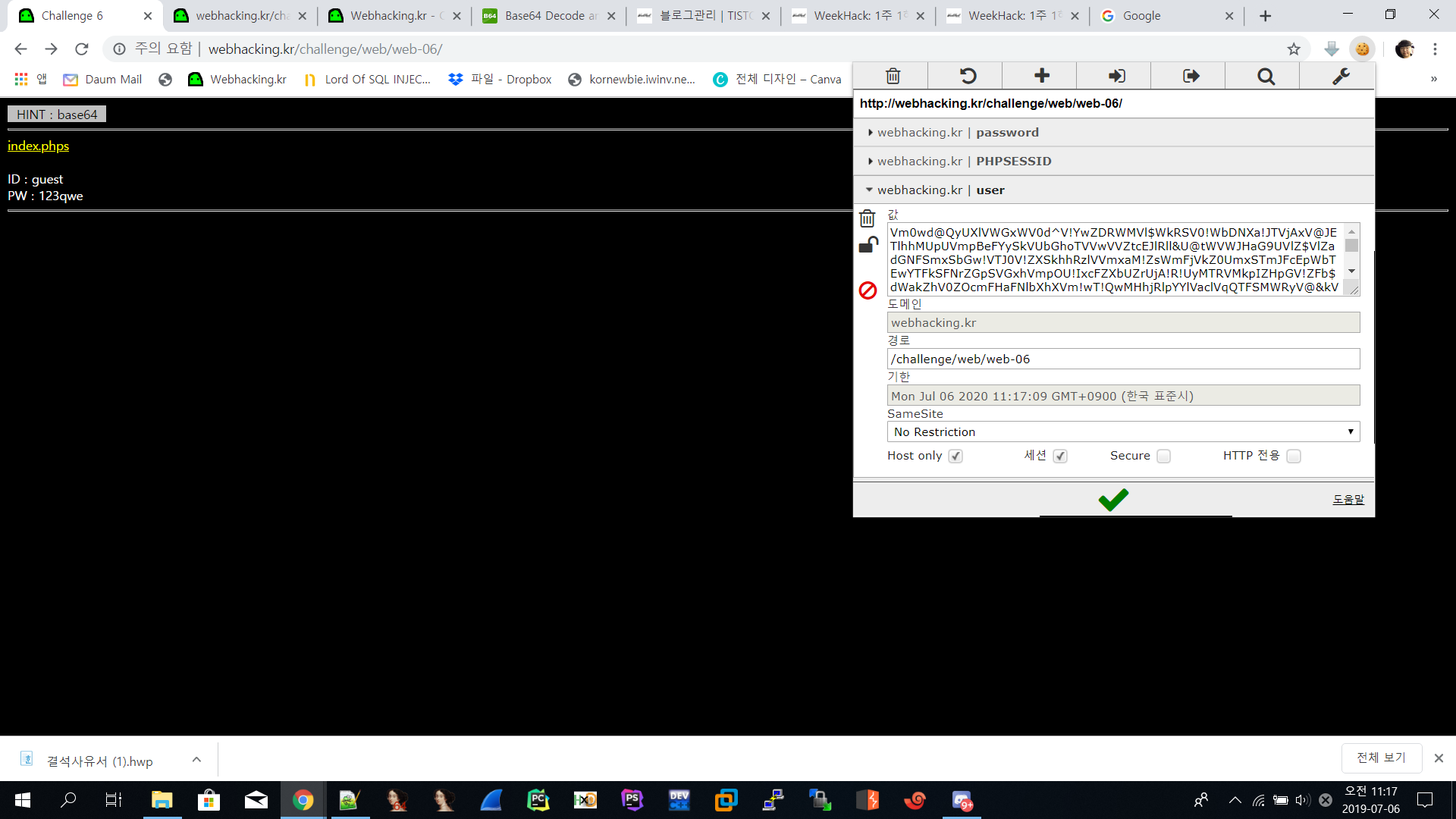

이렇게 solve가 됩니다.
이상입니다. 감사합니다!
반응형LIST